Whoa! I know that sounds dramatic. But here’s the thing. Solana’s grown fast, and wallets haven’t all kept pace. My gut said the same thing a year ago — somethin’ felt off when I watched apps ask for broad permissions, then cough up errors during staking. Initially I thought it was just a rough patch, but then reality set in: usability, security, and NFT tools are now the difference between a smooth session and a heart-sinking mistake.
Seriously? Yep. Why? Because the ecosystem is messy. There are dozens of DeFi dApps, each with slightly different signing patterns and approval flows. A clutch wallet experience smooths that friction, letting you stake, swap, and manage NFTs without second-guessing every click. On top of that, browser extension security is a recurring pain point — users often run extensions and just assume they’re safe. That assumption is dangerous though actually: malicious extensions and phishing overlays are real threats that target the smallest of lapses.
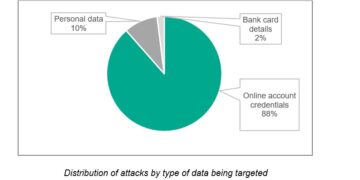
Here’s what bugs me about the status quo. Many wallets present the same checklist: send, receive, sign. But they bury context — like what exactly a program will be allowed to do after approval. A good wallet should explain program-level permission, show transaction history clearly, and let you revoke access quickly. I’m biased, but that’s very very important for anyone holding staked SOL or valuable NFTs. (Oh, and by the way… price charts are nice, but they don’t protect you when a drain happens.)
Quick story. I was testing a DeFi aggregator and the extension popped a permission modal that looked generic. Hmm… it didn’t show the actual program ID. I hesitated. Then I clicked details — and saw a repeated signature request that could have authorized recurring approvals. My instinct said “nope.” I closed the tab, checked the wallet’s connected apps page, and revoked it. Simple move. Saved me from what might’ve been a mess.

How browser extensions change the game
Browser extensions are convenient. They also widen the attack surface. Extensions sit between your keys and the web, and that middle layer must be minimal and transparent. If the extension injects UI into pages without clear origin labels, users can be tricked into signing transactions they don’t understand. So, what should a wallet extension do differently? Provide explicit program IDs, human-readable intent, and one-tap revocation that actually works across dApps and domains.
On a technical level, the best wallets compartmentalize permissions. They use session-limited approvals, origin restrictions, and clear UX cues when a dApp is requesting escalation. Initially I thought users would skip all those details, but trials show that once a wallet surfaces them clearly, people do check. Behavior changes when the info is digestible, not when it’s a wall of cryptic code. And for those who care, there should be an easy advanced-mode to audit raw transactions too.
Check this out—some wallets now show a human-readable synopsis of the instruction set before you sign. That’s huge. It reduces blind approvals. It also lets you spot commands that touch token accounts you didn’t mean to expose. Over time, those small UX wins reduce the exploit surface because attackers rely on user confusion.
Now let’s talk DeFi protocols on Solana. The chain’s low fees attract a ton of innovation, but it also attracts composability complexity. Farms call pools which call oracles which call token accounts — and when a transaction bundles many instructions, it’s easy to miss a risky step. A solid wallet unpacks those batches visually, labels each program, and flags anything that tries to move assets without explicit user intent. That extra layer of clarity matters when you’re staking significant amounts.
My approach to staking is conservative. I stake in small increments. I monitor validator stability. And I prefer wallets that let me manage staking accounts without forcing me to export keys or use CLI tools. Simplicity reduces errors. I’ll be honest: some tools claim advanced staking features, but they demand too much trust or too many manual steps. I’m not fond of that. Keep it simple, auditable, and reversible when possible.
Let me pause and note: managing NFTs is different from DeFi. NFTs are identity and social capital as much as value. Losing an avatar or a one-of-one collectible stings more than losing a lump-sum token sometimes. So wallet ergonomics for NFTs should prioritize clear provenance, signed metadata verification, and a safe transfer flow that prevents accidental listings or sales. That means clear confirmations, no hidden marketplace approvals, and a visible chain of custody for transfers.
On NFT management, the best wallets treat collectibles as first-class assets. They separate them visually from fungible tokens. They allow offline signing for high-value moves. And they integrate with marketplaces in a way that limits blanket approvals — again, session-limited and revokable. I’m not 100% sure of the perfect UI (honest), but the direction is clear: contextual safeguards beat after-the-fact chaos.
So where does the solflare wallet fit into this? From my hands-on time, it lands right in the middle of practical and user-friendly. The wallet gives you clear staking controls, integrates with major DeFi protocols, and has a browser extension that surfaces permissions more clearly than many competitors. It isn’t perfect, though — some advanced features still feel buried — but for most users balancing staking, swaps, and NFT management, it removes a lot of friction.
Okay, so check this out—when a wallet shows a connected apps list with quick revoke buttons, people actually use them. That’s a small behavioral win that compounds security. And when the extension separates signing requests by origin with color-coding or icons, it lowers phishing risk. These are the details you notice after using a wallet for months, not minutes.
On developer-facing features, good wallets expose readable error messages and program info so builders can debug without leaking private keys. For dApp authors, that reduces support tickets and accidental permission prompts, which improves user retention. On Main Street, this equals less confusion and fewer “where did my tokens go?” reports on Discord at 2 AM.
There are trade-offs. Ultra-secure setups like hardware-only flows can be cumbersome for active DeFi users. Conversely, convenience-forward extensions risk broad permissions. The smart middle ground uses a hybrid: keep keys secure, but let users sign low-risk actions quickly while gating high-risk operations behind stronger confirmations. On one hand that’s more complex to build. On the other hand, it’s what real people need when juggling staking and NFTs across marketplaces and farms.
Common questions
How should I evaluate a wallet for DeFi use?
Look for clear permission UIs, session-scoped approvals, and easy revocation. Prioritize wallets that unpack batched instructions so you can see each program involved. Also test the staking UX—can you delegate and undelegate without CLI steps? If yes, good sign. And always consider hardware integration for larger balances.
Are browser extensions safe for high-value NFTs?
They can be, but prefer wallets that support offline signing or hardware confirmations for high-value transfers. For everyday browsing, an extension with origin restrictions and explicit permission reviews is fine. But for one-of-one moves, I personally go hardware or cold-sign. It feels safer, even if it’s slightly slower.